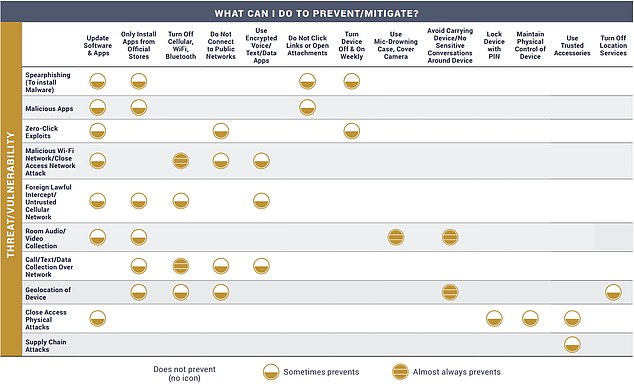
Anyone with an iPhone or Android should turn their device on and off once a week, officials say, to protect themselves from hackers.
The idea is to protect against no-click exploits, which allow hackers to load malicious apps, spyware, and phishing scams on devices without users clicking on links.
The National Security Agency (NSA) has urged users to restart their phones at least once a week and turn off WiFi and Bluetooth to prevent personal data theft.
The NSA also warned that users should be careful when connecting to public WiFi networks and are advised to update their phones’ software and apps regularly.
The NSA warned that the advice is not 100 percent effective, but will provide at least partial protection against certain malicious activities.

Android and iPhone users have been asked to restart their phones once a week and turn off WiFi and Bluetooth to avoid cybersecurity attacks. Criminals can use no-click exploits to infect a device and collect data without requiring the user to click a link or download a file.
An NSA document lists the numerous steps iPhone and Android users should take to mitigate the risk of a cyberattack.
Restarting your phone is one of the lesser-known methods to combat cyberattacks, but it’s also important to update software and apps frequently to ensure your device is safe.
By turning the phone off and on again, users reduce the chance of phishing, when an attacker sends fraudulent emails aimed at stealing sensitive information, such as login credentials.
Over time, hackers find new ways to break into a system, but updating old software will eliminate any potential flaws or loopholes they may have used to access your data.
The NSA also recommended that people turn off their Bluetooth when they are not using it because it reduces the chance of people gaining unauthorized access to their devices.
The advice is not 100 percent effective, the NSA warned, but it should provide partial protection against certain malicious activities.
“Threats to mobile devices are more frequent and increasing in scope and complexity,” the NSA warned, adding that some features of smartphones “offer convenience and capability but sacrifice security.”
Users should also turn off their WiFi and remove unused networks that cybercriminals can use to attack their phones.
When connecting to a WiFi network, it is important to watch out for SSID confusion attacks that trick users into connecting to your hotspot instead of the establishment’s official WiFi using a similar network name.

The NSA recommended that people turn off their Bluetooth when they are not using it because it reduces the chance of people gaining unauthorized access to their devices.
A strong lock screen with a minimum six-digit PIN will add much-needed protection when combined with the feature that prompts the smartphone to wipe itself after 10 incorrect attempts.
It further warned that people should avoid opening email attachments or links from an unknown source that could install malicious software without the person’s knowledge.
“Falling into social engineering tactics, such as responding to unsolicited emails requesting sensitive information, can result in account compromise and identity theft,” said Oliver Page, CEO of cybersecurity company Cybernut. Forbes.
‘These phishing attempts often imitate legitimate entities, tricking people into revealing sensitive details.
“Relying on unverified phone calls or messages can have serious consequences, as scammers manipulate victims into revealing sensitive information or taking actions that compromise their safety.”
The Federal Communications Commission (FCC) also users warned against dismantling any security settings that could give cybercriminals the opportunity to access the phone.
“Tampering with your phone’s factory settings, jailbreaking, or rooting your phone undermines the built-in security features offered by your wireless service and your smartphone, while making you more susceptible to attack,” the company warned. FCC.
According statesmanThe data of 353 million people was compromised in the US last year, including breaches, leaks and exposures.