A lethal, flesh-rotting animal tranquilizer is now abundant in cocaine sold in Britain, experts warn.
Xylazine, nicknamed “tranq,” has helped turn American cities like Philadelphia and New York into “zombie lands,” leaving its users lifeless.
But the powerful drug, strong enough to knock out elephants, is now widespread on the streets of the UK.
It has already been linked to 11 deaths, but experts say this could be the tip of the iceberg and hundreds more could die in the coming years.
Investigators found tranquilizers in supplies of strong opioids such as heroin and fentanyl.

Karl Warburton, 43, (pictured) died in May 2022 from the effects of xylazine combined with other drugs, including heroin, fentanyl and cocaine.
Traffickers use the substance as a cutting agent to make medications even more potent than they already are, as well as to expand supplies.
Academics at King’s College London also found tranquilizers in cocaine, counterfeit codeine and Valium tablets and some cannabis e-cigarettes.
Experts warned that this showed the extent to which tranq has penetrated Britain’s drug supply, without users knowing they are buying drugs laced with the tranquilliser.
Tranq can rot the body from the inside out and cause ulcers in people who inject the medication directly into the blood.
Analysis of the toxicology report has linked tranq to 11 deaths in the UK since 2022, most of which occurred last year.


A powerful animal tranquilizer that has helped turn some US cities into “zombie lands” is being added to the UK’s cocaine supplies, experts have warned.
This is believed to include Karl Warburton, a 43-year-old factory worker who became the first known victim of the tranquilizer in the UK in 2023.
The researchers warned that the figure of 11 is likely a “gross underestimate” given that UK laboratories have not routinely tested for the drug.
Many of the people included in the toxicology reports also tested positive for cocaine use.
In an article in Addiction magazine, experts warned that if tranq use explodes like it does in the United States, hundreds of Britons could die.
“If the UK were to experience a 20-fold increase in deaths seen in the US since 2015, deaths following xylazine use could be anticipated to exceed 220 deaths by 2028,” they said.
Xylazine was originally developed as an animal tranquilizer in the 1960s, typically for large animals such as cows and horses.
It binds to and blocks adrenergic receptors in the brain, which release the stress hormones norepinephrine and dopamine, effectively slowing down brain activity.
The result is a reduction in pain and stress, as well as a feeling of euphoria similar to that of opioids.
As such, its powerful narcotic effects can dangerously reduce people’s heart rate and breathing.
Lead author Dr Caroline Copeland, a toxicology expert, said: “We now know that xylazine has penetrated the UK illicit drug market.
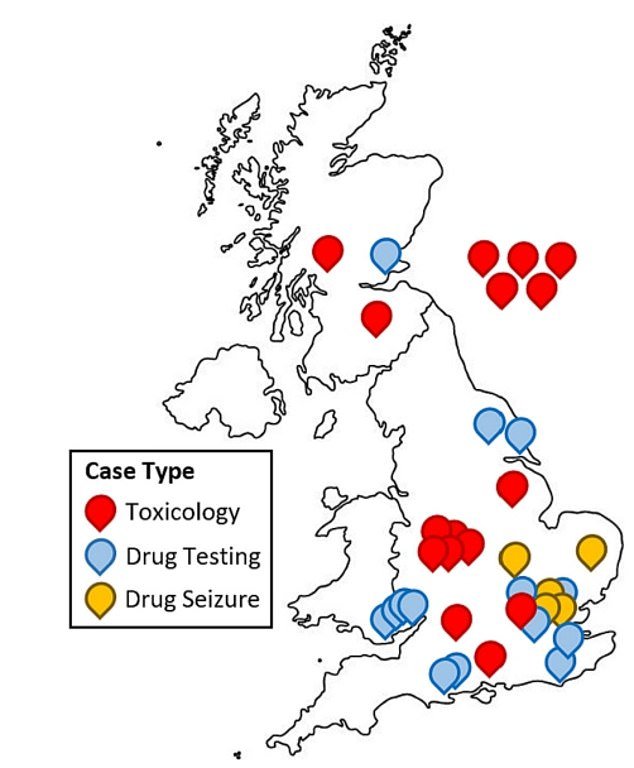

This map shows where xylazine has been detected in the UK in a combination of toxicology reports in people, as well as samples taken from drugs tested or seized by authorities. Locations are approximate to the county or city reported. Five toxicology cases where the location was completely redacted are located on the right of the map, and two cases whose location is only listed as Scotland are located randomly in the country.


Xylazine depresses the central nervous system, causing users, like these in the Kensington neighborhood of Philadelphia, to appear zombie-like.


The flesh-eating drug can affect a person’s skin in places other than the injection site. This patient often injected the drug into his neck with gruesome effects.
“This is cause for alarm, as a much broader population of people who use drugs in addition to heroin users will be exposed to their harms.”
He called on the UK to implement three measures to prevent a reassuring “epidemic” similar to that which has hit the United States.
“Cheap xylazine test strips should be made available, healthcare providers should be aware of signs that chronic skin ulcers are due to xylazine use, and pathologists and forensic pathologists should specifically request toxicology testing for xylazine in patients. relevant cases to understand the true prevalence of xylazine”. drug,’ she said.
In addition to examining toxicology reports, Dr. Copeland and his team also examined 14 drug samples that had tested positive for tranquilizers.
Two of them were for vaping THC (the psychoactive component of cannabis), and the rest were counterfeit pain relievers, sleeping pills and anti-anxiety pills.
The rise of Tranq in the United States, where the powerful sedative is mixed with stimulants such as cocaine and methamphetamine, is credited with creating “zombies” on the streets of major cities such as Philadelphia, New York, Sacramento and Portland.
The combination of sedative and stimulant turns users into human statues that exist in a zombie-like state instead of completely passing out.
Its other famous effect is a “flesh rotting” quality seen among people who take it.
While not fully understood, the theory is that tranq constricts blood vessels, slowing or blocking the flow of oxygenated blood throughout the body.
This can prevent major and minor injuries, including medication injections, from healing properly, increasing the risk of infection.
Its presence in cocaine is particularly worrying for the UK, as Britain has the highest consumption of the drug in Europe.
One in 40 adults (2.7 per cent) in the UK takes the class A drug, more than any other country in Europe, according to figures from the Organization for Economic Co-operation and Development.
Cocaine, once the exclusive domain of high society, is now widely used throughout British society.
This is due, in part, to the fact that its price has fallen in real terms over the last decade since in many places in the country it can be delivered “as fast as a pizza.”
Separate data from the Office for National Statistics shows that cocaine-related deaths have increased eight-fold in the last decade and have increased for ten consecutive years.
In 2021, 840 people died in England and Wales due to cocaine, up from 112 deaths in 2011.
Your browser does not support iframes.


One in 40 adults in the UK takes the class A drug, a figure more than any other country in Europe and behind only Australia globally.
Your browser does not support iframes.
Your browser does not support iframes.
Meanwhile, the number of older people treated for cocaine abuse in hospitals in England rose sharply last year, according to NHS data.
Those over 60 years old, nicknamed “silver snorters,” were admitted 540 times. Among them were 85 between 70 and 79 years old, 11 between 80 years old and three between 90 years old.
Experts have said the high rate of cocaine use in the UK is due to the drinking culture in Britain, with many taking the stimulant to counteract the sedative effects of alcohol.
Tranq, which is cheaper than many other illicit substances and costs as little as £5 per kg, is often added to the prProvide a more powerful kick for users.
Combining in this way also allows distributors to expand their offerings and hook users more easily, providing a cruel and profitable cycle of repeat customers for distributors.
There is no approved antidote for tranquilizer overdoses in humans; instead, treatment focuses on counteracting the effects of the drug.
