Security experts issued a warning to Google Chrome users after discovering a cyberattack targeting the browseras well as microsoftWord and OneDrive applications
The attack has used fake error messages to trick users into installing the malicious software themselves as a “fix.”
Hackers send email notifications and pop-ups on websites, claiming that the user has experienced a software malfunction and needs a quick update.
To detect a fake, experts have advised users to be wary of messages claiming that a fix will require them to install a “root certificate” by copying and pasting raw code.
While the cyberattack is capable of stealing all types of private digital data, some of the new malware appears poised to steal cryptocurrencies, such as bitcoin.
Hackers have a new tactic to get malware onto your computer: fake updates to Google’s Chrome browser, as well as Microsoft’s Word and OneDrive products.
The malicious new hacking tactic was discovered by the prolific cybersecurity company Proofpoint, founded in 2002 by a former Netscape CTO.
The new style of “fake error messages,” they warned, “is clever and pretends to be an authorized notification coming from the operating system.”
The scheme involves seemingly official prompts from these tech giants, Google and Microsoft, asking users to open what is known as a ‘command-line shell’, specifically Microsoft’s version of a command-line tool for Windows. , PowerShell.
Command-line tools, including Windows PowerShell, are programs designed to let more experienced coders directly program the core code of their own computer.
Fake error messages from hackers encourage unwitting users to copy and paste raw code and then install it as a “fix” by running or “running” that code in PowerShell.
Cybersecurity experts have only seen these hackers implement this specific ‘fake workaround’ scheme via PowerShell, so Apple iOS users should be able to rest easy for now.
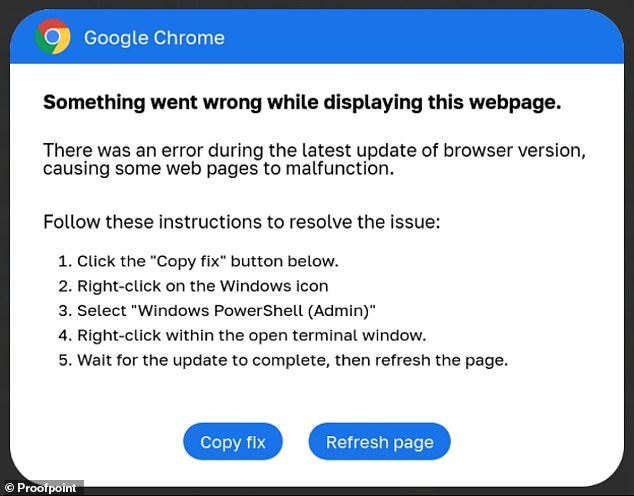
The scheme involves seemingly official prompts, like the one shown above, that ask users to open what is known as a “command-line shell,” a form of software that allows more experienced programmers to program their computer in a way more direct and install a code solution. ‘
“This attack chain requires significant user interaction to be successful,” the company noted in your advice post on PowerShell based cyber threat.
“It also provides both the problem and a solution,” they noted, “so the viewer can take action quickly without stopping to consider the risk.”
Any person or message telling you to run raw code in a terminal or shell should be treated with caution and extreme skepticism, they said.
In all cases, these hackers have created their fake error messages through flaws or vulnerabilities inherent in the use of JavaScript in HTML email attachments or through fully compromised online websites.
While fake overlapping errors from Google Chrome, Microsoft Word, and OneDrive have been documented, Proofpoint researchers warned that this basic form of hacking could present itself as other legitimate software update requests in the future.
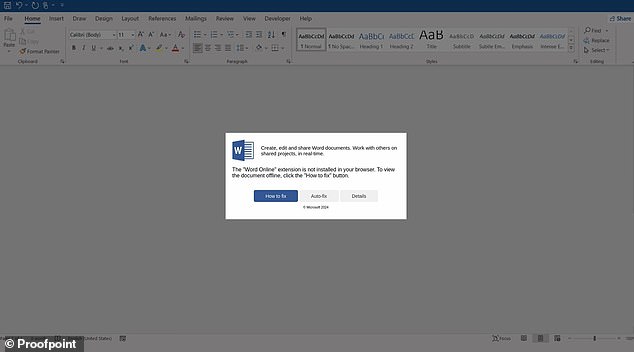
In all cases, cybersecurity experts explained, hackers created their fake error messages through flaws or vulnerabilities using JavaScript in HTML email attachments or through compromised websites. Above, an example of fake messages, this time disguised as an MS Word message.
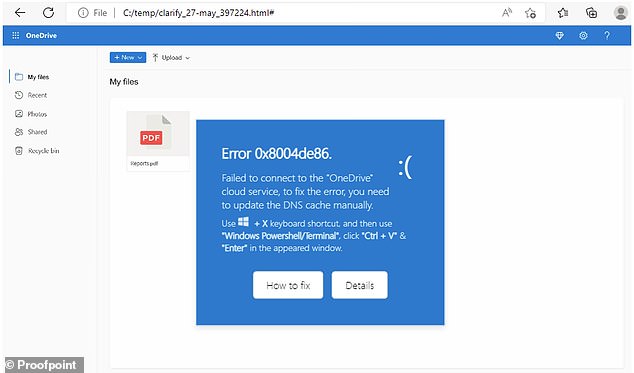
While fake overlapping Google Chrome, Microsoft Word, and OneDrive errors (example pictured above) have already been documented, Proofpoint researchers warned that this basic form of hacking could present itself as other trusted software update requests in the future.
According to Proofpoint, two interesting malware programs gave clues to the hackers’ intentions.
One called ‘ma.exe’ downloaded and ran a cryptocurrency mining program called XMRig with specific settings. The second, ‘cl.exe’, was cleverly designed to replace cryptocurrency addresses in the user’s ‘cut and paste’ clipboard.
Essentially, that second malware program was intended to accidentally cause unsuspecting victims to “transfer cryptocurrency to an address controlled by a threat actor instead of the address intended when making the transfers,” the Proofpoint team said.
If a user were copying and pasting a cryptocurrency wallet address to send their digital money, this malware would silently change that copied address to the address of its own fictitious wallet.
When the hack is successful, the user is unaware of the change and simply sends the cryptocurrency cash to the hacker’s anonymous dummy wallet.

In April, security experts saw this new method in use alongside hacking tools group ClearFake, which targeted Apple users last November with what was described as a “one-hit-to-smash-and-capture” virus. “. New hacks appear poised to steal users’ cryptocurrencies
In April, security experts saw this new method in use alongside hacking tools group ClearFake, which targeted Apple users last November with what was described as a “one-hit-to-smash-and-capture” virus. “.
The hacker’s malicious PowerShell script acts as a Trojan, allowing even more malicious code to be downloaded onto the victim’s system.
First, it supposedly performs various diagnostics to confirm that the host device is a valid target.
As a key test, one of the malicious PowerShell scripts would obtain the system temperature of the victim’s computer to detect whether the malware was running on a real computer, or in a so-called “sandbox”, an isolated virtual PC that It is used to handle and analyze potentially dangerous software.
If no temperature data was returned to the malware, that fact was interpreted as a signal revealing that the hacker’s code was actually running within a virtual environment, or sandbox.
The malware would then exit and abort its operation, protecting later, more detailed malicious code from hackers from being trapped in the sandbox for experts to study.
The Proofpoint team advised users to be careful when copying and pasting code or other text from messages on websites or alerts that purport to come from trusted software applications.
“Antivirus software and EDRs (endpoint detection and response monitoring software),” they said, “have trouble inspecting clipboard contents.”
The cybersecurity firm also called on companies to conduct training on this topic and focus on “detection and blocking” that would prevent these and similar “fake solutions” messages from appearing in the first place.


