Giant asset managers are becoming titans of Wall Street and increasing their control over the US financial system.
Huge investment firms now reportedly control twice as many assets as the once-dominant US banks, managing sums that rival the economies of major countries around the world.
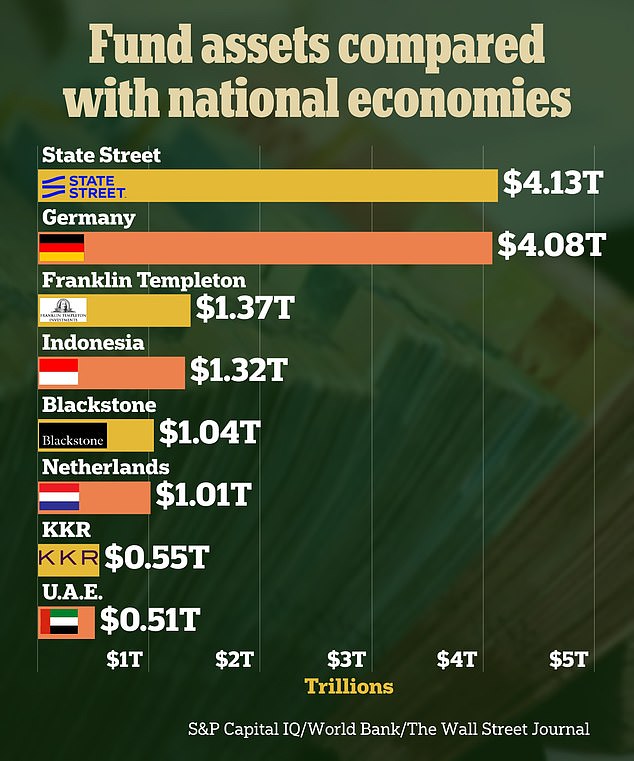
Assets held by Boston-based fund manager State Street in 2023 amounted to $4.13 trillion, according to The Wall Street Journal.
This was more than Germany’s gross domestic product (GDP), which was $4.08 trillion in 2022.
New York City-based investment management firm Blackstone had $1.04 trillion in assets last year, more than the Netherlands’ GDP of $1.01 trillion in 2022.
Huge investment firms now manage sums that rival the economies of major countries around the world, The Wall Street Journal reported.
The funds manage assets for pension plans, wealthy individuals and companies.
These fund management companies are offering new types of products to capture market share, The Wall Street Journal reported.
The largest ones are becoming so-called “financial supermarkets,” offering products not only for the wealthy and large institutions, but also for middle-class investors.
Asset managers are also replacing banks as lenders to American businesses and consumers, he reported, and forming deals with insurance companies to drive growth.
Four of the largest public fund managers (BlackRock, Fidelity, State Street and Vanguard) control around $26 trillion, which is equivalent to the entire annual economic output of the United States.
This growth began after the 2008 financial crisis.
New regulation introduced after the crisis meant that investments and lending by major US banks were more controlled, leaving room for funds under management to grow.
Central banks kept interest rates low for the next decade, driving investors away from savings accounts and Treasuries and toward managed funds.
According to an analysis by The Wall Street Journal, major US banks and fund managers had approximately $12 trillion in assets in 2008.
Today, however, asset managers, private money managers and hedge funds control about $43.5 trillion, almost double the $23 trillion held by banks.
Big banks have responded to this by becoming more fund managers and strengthening their investment teams, the outlet reported.
Earlier this month, Goldman Sachs reported revenue of around $4 billion from asset and wealth management in the first quarter of 2024, double the profit of its investment banking division.
And last week revenue at Bank of America’s wealth business also rose, gaining 5.2 percent to $5.59 billion, in a record quarter for the division.
This was driven by “increased asset management flows”, said chief financial officer Alastair Borthwick.

Giant asset managers are becoming titans of Wall Street and increasing their control over the US financial system.

Four of the largest public fund managers (BlackRock, Fidelity, State Street and Vanguard) control around $26 trillion, equivalent to the entire annual economic output of the United States (pictured: Larry Fink, CEO of BlackRock ).
Private equity funds, in particular, have seen significant growth in recent years.
A private investment fund is an investment company that does not solicit capital from retail investors or the general public.
According to The Wall Street Journal, the assets of private or “alternative” investment funds have doubled to nearly $6 trillion in the past four years, outpacing the 31 percent growth of public funds.
Private equity fund managers ranked 41st on the Forbes list of American billionaires released this month, more than any other profession.
This increase means that there are new risks that the markets have not faced before.
The Securities and Exchange Commission (SEC) last year approved new rules for private funds to increase transparency and crack down on funds that offer special offers, known as “side letters,” to specific investors.