<!–
<!–
<!– <!–
<!–
<!–
<!–
The Supreme Court seems skeptical of limiting access to the abortion pill mifepristone nationwide, but if it rules in favor of the Food and Drug Administration, that doesn’t mean the pill will be universally available in the United States.
The justices heard oral arguments in the pivotal case FDA v. Alliance for Hippocratic Medicine on Tuesday and will likely issue their decision in late June or early July before going into recess.
The ensuing case has the potential to affect abortion access not only in states that have taken steps to further restrict or ban abortion since Roe v. Wade was overturned. Wade in 2022, but also in states where the right to abortion is protected or even expanded.
Fourteen states already have near-total bans on abortion, so those states would not be greatly affected by the decision because their laws already prevent medical abortion in almost all cases.
More than a handful of other states had passed other restrictions since the fall of Roe, including bans on abortion from six weeks to 18 weeks, which could see some access affected if the pill mifepristone were further limited.
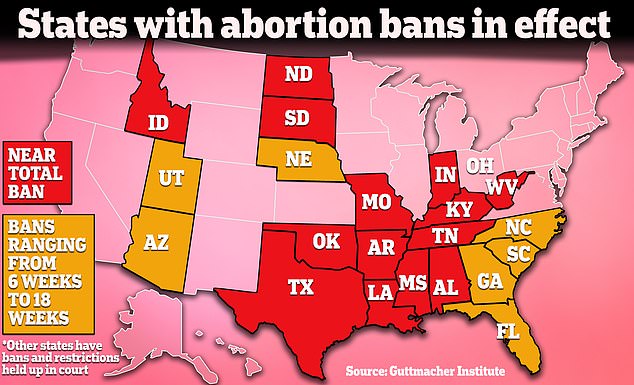
Limiting access to the abortion pill would have less impact in states with near-total abortion bans because abortion is already completely blocked in most cases. It could have some impact in states where there are more restrictions on the books depending on the states.
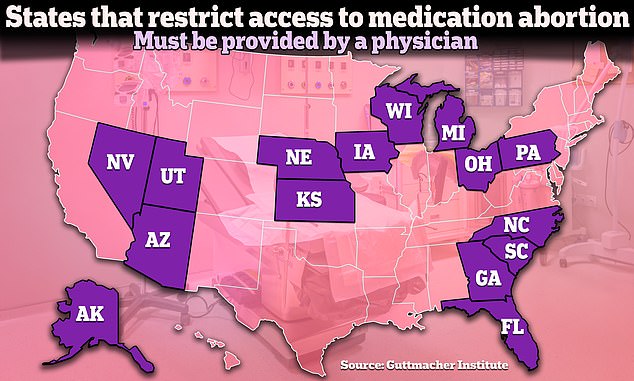

At least fifteen states have restrictions on medical abortion that require the pill to be distributed by a doctor. Several have other restrictions, such as prohibiting mailing pills or requiring an in-person visit to a doctor. Several other states have such restrictions held up in court.
Mifepristone is part of a two-drug process to end a pregnancy. First, a person uses mifepristone followed by the medication misoprostol. The drug is currently approved for abortion during the first 70 days or up to 10 weeks of pregnancy, a change made in 2016.
According to the Guttmacher Institute, a pro-abortion rights research organization, 15 states, not including states with near-total abortion bans, currently have additional restrictions specifically on medication abortion already in place beyond the rules of the FDA.
The most common of the restrictions is requiring that the abortion pill be provided by a doctor.
In 2016, the FDA expanded who could prescribe the abortion pill beyond doctors to include people like nurse practitioners and physician assistants. But currently, fifteen states have laws requiring it to be provided by a doctor.
The FDA also changed in-person disbursement requirements in 2021 amid the coronavirus pandemic, but at least five states have laws requiring patients to have an in-person visit with a doctor.
Additionally, Wisconsin requires patients to receive the first dose in the presence of a doctor, and Arizona has a ban on mailing abortion pills.
In 2023, the FDA also approved allowing pharmacies to dispense mifepristone directly to patients.
But as the case over access to abortion pills reached the Supreme Court, states where abortion access had been expanded warned that this would affect them too, and some states began taking precautionary measures.
As these states began to face the possibility of restrictions on abortion pills being reimposed, some began stockpiling drugs used in medical abortion last year.


Several states began stockpiling abortion pills, including mifepristone and misoprostol, amid concerns that access to abortion pills would be limited or blocked with the Alliance for Hippocratic Medicine lawsuit.
Massachusetts Gov. Maura Healey said last year that her state had enough doses of mifepristone in storage to last more than a year.
In California, Governor Gavin Newsom revealed that the state had a stockpile of up to two million pills of misoprostol, the other drug used in medical abortion.
In Washington state, Gov. Jay Inslee said the state was also stockpiling generic mifepristone.
Last June, Maryland also approved the purchase of abortion pills for a state stockpile. In August of last year, Hawaii had also begun stockpiling abortion pills.
In New York, Gov. Kath Hochul announced last spring that the state would stockpile 150,000 doses of misoprostol, a five-year supply, amid fears that access to abortion pills would be blocked.
