A world-renowned hacker has revealed why you should never use an iPhone charger that you didn’t buy yourself, as it could allow people to steal your data.
Ryan Montgomery is a cybersecurity professional hired by companies and organizations to test their digital systems for vulnerabilities.
he was He was ranked number one on popular cybersecurity training site TryHackMe for his skills.
Montgomery explained how a totally normal-looking iPhone charger can actually “wreak havoc on your computer or phone.”
That’s because the insidious cable features a hidden implant with a web server, USB communications, and Wi-Fi access, allowing you capture keystrokes, steal credentials, exfiltrate data, and even plant malware.
This deceptive hacking device, called the ‘O.MG cable’, became publicly available in 2019 when it went on sale for just $180.
In a video posted to his Instagram, he plugged what appeared to be a regular charger into a “new” computer. “This is a fully functional cable, you can still charge a phone with it,” he said.
But “with this cable connected, I have full access to this computer,” he explained.
Without even plugging his iPhone into the other end of the cable, he gained remote access to the computer by pressing a single button on his phone.
World-renowned ‘ethical’ hacker Ryan Montgomery has revealed why you should never use an iPhone charger that you haven’t bought yourself, as it could allow people to steal your data.
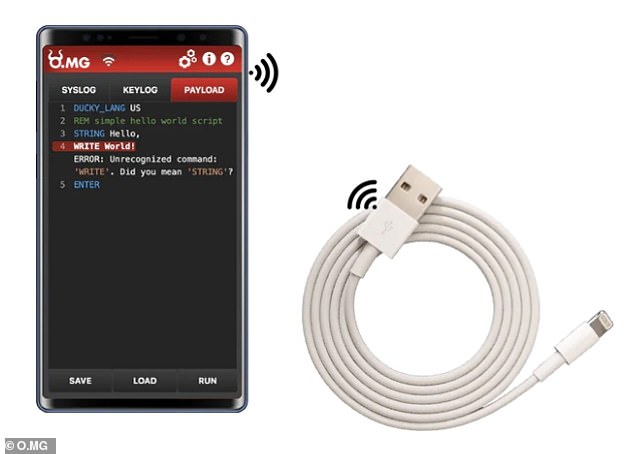
The O.MG cable looks and behaves just like a regular Apple charger, but contains a wireless implant that can be accessed by a nearby hacker.
‘It is designed to allow your Red Team to emulate sophisticated adversary attack scenarios. Until now, a cable like this would cost $20,000,” Hak5, which sells the device, says on its website.
A ‘Red Team’ is a group of cybersecurity professionals who simulate real hacks.
The cable’s creator, security researcher Mike Grover, has said: “It’s a cable that looks identical to the other cables you already have.”
‘But inside each cable, I place an implant that has a web server, USB communications and Wi-Fi access. So you plug it in, it turns on, and you can connect to it.”
He claimed that the cable could allow you to access a device from up to 300 feet away, and if you configured the cable “to act as a client for a nearby wireless network,” the distance would be unlimited.
Not only is it impossible for a person to know if they have stumbled upon one of these tricky cables, but there is almost no way to know when you are under active attack.
For this reason, the O.MG cable has been called “the most dangerous USB cable in the world.”
Worryingly, the capabilities of the O.MG cable are becoming more sophisticated.
Grover said Forbes that the newly launched ‘Elite series’, launching in 2023, comes in multiple form factors including USB-A cables, USB-C cables, USB-A to -C adapters and, surprisingly, USB data blockers, so Even these protection devices could be secretly malicious.
And the upgrades included in this latest series are the ones that added data exfiltration (or the ability to steal data) to the cables’ stealth specifications.
Although the O.MG cable could easily be obtained and used by someone with malicious intent, it is actually designed for professional hackers like Montgomery, who test data systems for vulnerabilities.
Because of this, Grover has equipped the cables with some safety nets, such as allowing a Red Team to restrict the cable’s access range to a specific location.
When this feature is enabled, removing it from that area will cause it to stop working or self-destruct.
Additionally, Grover designed the cables so that they do not sync or charge when armed, reducing the window for undetected attack when connected to a smartphone.
But it looks like some evil hackers have already gotten their hands on the O.MG cable. In 2023, the FBI stated: “Bad actors have discovered ways to use public USB ports to introduce malware and tracking software to devices.”
The Federal Communications Commission (FCC) also previously issued a warning about ‘juice jacking,’ when hackers weaponize charging stations with USB ports, such as those found in airports or hotel lobbies, to steal your data. .
But in this scenario, it’s not the cable that hacks your device, but the outlet itself. Although this has been shown to be technically possible, cybersecurity experts say the risk to the public is nominal.
The O.MG cable, however, represents a very real threat. For this reason, experts have advised against using any charger that you have not purchased, as it could be compromised.

