The US Treasury Department imposed sanctions on a Chinese company on Monday, accusing it of being a front company for “dangerous and irresponsible” state-sponsored hacking.
The announcement adds to seven indictments issued by the Department of Justice accusing seven men affiliated with that company, Wuhan Xiaoruizhi Science and Technology Company Ltd. (Wuhan XRZ), of “malicious cyber operations.”
The Wuhan XRZ cyberattacks, officials said, were part of a widespread effort to introduce malware into critical American public services, including power grids and water supplies.
Although the presence of this software, buried within critical US infrastructure, has not yet led to an offensive cyberattack, intelligence officials believe Beijing had installed the malicious code in an effort to thwart US efforts to defend Taiwan.
This afternoon, the US State Department, which collaborated with the FBI and the Department of Justice in the hacking investigation, announced a reward of 10 million dollars to obtain “information about the group and the defendants” as part of its Rewards for Justice program.

The US Treasury Department imposed sanctions on a Chinese company on Monday, and the Department of Justice (DOJ) issued indictments against seven alleged hackers involved, accusing the company of being a front company for “dangerous and irresponsible” cyber warfare. “sponsored by the State.


Above, photos of the Justice Department indictment: (top left to right), Ni Gaobin, Weng Ming, Cheng Feng, (bottom left to right) Peng Yaowen, Sun Xiaohui, Xiong Wang and Zhao Guangzong
In recent years, Biden administration officials and federal law enforcement, including FBI Director Christopher Wray, have devoted considerable resources to carrying out a Chinese government covert operation they have dubbed ‘Volt Typhoon’. .
The nickname describes an alleged Chinese hacking network that researchers say has infiltrated more than 20 major nodes of American infrastructure in the last year alone.
Their successful goals, according to government officials who spoke anonymously with Washington PostThey have included a water company in Hawaii, a major West Coast port and at least one oil and gas pipeline.


China’s cyberattacks have grown to a “larger scale than we’ve seen before,” FBI Director Christopher Wray warned this year, amid fears that American infrastructure is under threat.
Today’s seven indicted and indicted hackers linked to Wuhan .as ‘Advanced Persistent Threat 31’ or APT31.
The seven hackers accused of APT31, Ni Gaobi, 38; Weng Ming, 37 years old; Cheng Feng, 34 years old; Peng Yaowen, 38 years old; Sun Xiaohui, 38 years old; Xiong Wang, 35 years old; and Zhao Guangzong, 38, also allegedly attacked US government officials as well as public infrastructure.
Justice Department officials said the group used “sophisticated” means to also hack economic and defense companies, hiding codes in more than 10,000 so-called “phishing” or “spear-phishing” emails.
APT31, according to the FBI and the Department of Justice, targeted these companies, as well as political and government officials, candidates and campaign staff over the past 14 years.


The Director of National Intelligence warned in February 2023 that China is already “almost certainly capable” of launching cyberattacks to disable oil and gas pipelines and rail systems.


Analysts believe the Chinese military has shifted its strategy from intelligence gathering to infiltration in an attempt to sow chaos should war break out.
“The Department of Justice will not tolerate the Chinese government’s efforts to intimidate Americans who serve the public, silence dissidents who are protected by American laws, or steal from American businesses,” Attorney General Merrick Garland said Monday in a statement.
“This case serves as a reminder of the lengths to which the Chinese government is willing to go to attack and intimidate its critics, including launching malicious cyber operations intended to threaten the national security of the United States.”
The joint sanctions issued by the US Treasury Department were part of an international effort with partners in the UK to crack down on Chinese piracy in essential services.
treasury officials described the work of state-sponsored malicious cyber actors as “one of the largest and most persistent threats to the national security of the United States.”
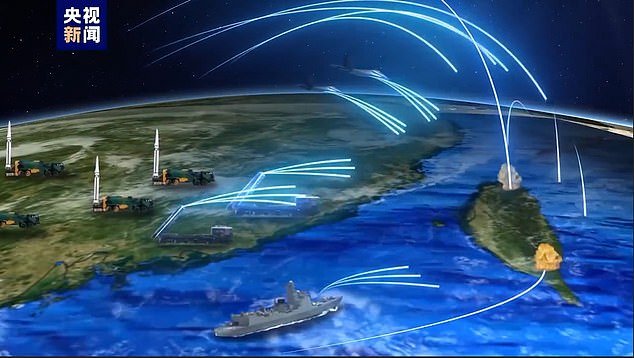

Although the malicious code, buried within critical US infrastructure, has not yet led to a cyberattack, US intelligence officials believe Beijing planted it to thwart US efforts to defend Taiwan. Above, still image from an animated video shared by China’s military in spring 2023, simulating how China would launch an all-out attack on Taiwan.
According to Treasury Department investigators, suspected APT31 hackers affiliated with Wuhan XRZ have been responsible for some of China’s most malicious cyber operations, including a 2020 spear-phishing operation targeting the US Naval Academy. and the China Maritime Studies Institute of the US Naval War College.
The operation, according to court documents, suggestively followed public comments by a US State Department official in 2020, who described Chinese military actions near Taiwan in the South China Sea as “completely illegal.”
In another example, hackers are accused of attacking the Norwegian government after the Scandinavian country awarded its famous Nobel Peace Prize to activists from Hong Kong’s democracy movement.
A series of reports from U.S. intelligence agencies have argued that Chinese military strategists hope to force the United States to move away from Taiwan and focus on its own disaster management, directing U.S. military and logistics toward domestic concerns of electricity, food and water. , in case of a Chinese attempt to retake the island nation.
Taiwan’s independence and its past history as part of China have been a point of tension between the United States and the Asian superpower since the dawn of the Cold War in the years after World War II.
