Joey Barton claimed police visited him three times in the last four days and criticized “attempts to intimidate me and my family” before comparing the UK to North Korea.
The former Manchester City and Newcastle footballer revealed that some of his tweets led to multiple police visits to his home this week, and the officer asked him for a voluntary interview.
He said the visits occurred while his children were sleeping and criticized any attempts to “intimidate” his family, saying the methods were similar to something in North Korea.
Barton married his childhood sweetheart, Georgia McNeil, in 2019. The couple has four children together: Cassius, born in 2011, Pieta, born in 2014, Penn, born in 2018, and Etienne, born in 2022.
“Cheshire Police have visited me 4 times in 3 days,” he said in X, later adding “it’s either a disaster or an attempt to intimidate me and my family.” Welcome to North Korea.’
Joey Barton has claimed police visited him at his home four times in three days over his controversial tweets.
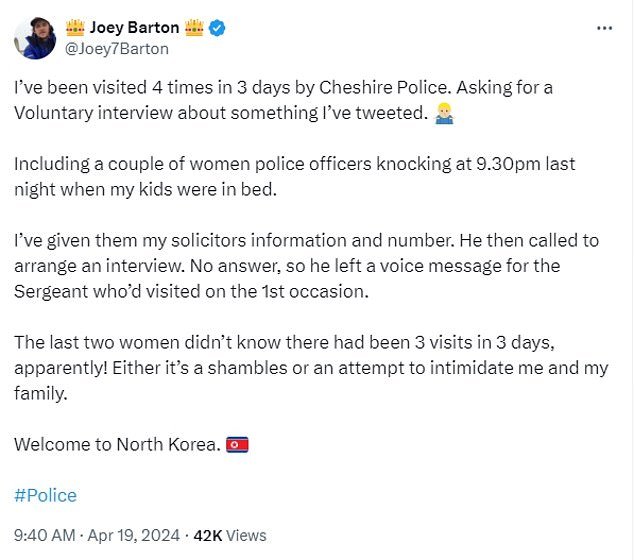
Barton told his 2.8 million followers on X: ‘Cheshire Police visited me 4 times in 3 days. Asking for a voluntary interview about something I tweeted,”
‘Including a couple of policewomen who knocked on the door last night at 9.30pm when my children were in bed. I have given you the information and number of my lawyers. Then he called to set up an interview. There was no response, so he left a voicemail for the sergeant who had visited him on the first occasion.
‘The last two women didn’t know that there had apparently been 3 visits in 3 days! It’s either a disaster or an attempt to intimidate me and my family. Welcome to North Korea.’
Barton has kept her relationship with McNeil private, but the couple married during a ceremony at the Aynhoe Park estate in Oxfordshire in 2019.
In 2021, Barton was accused of “kicking his wife in the head” and causing a “golf ball-sized lump” during a fight at their home in Kew, south-west London.
However, in 2022, McNeil recanted his accusation and opted not to press charges after admitting that he was “drinking a lot” and got the details wrong.

Barton has launched repeated tirades against female broadcasters and football players in recent weeks.

Partick Thistle goalkeeper Ava Easdon was the focus of Joey Barton’s ire last month after the 17-year-old played for her team in the Sky Sports Cup final.
Barton has come under fire this year for his tweets about women working in men’s football, infamously claiming that female pundits “shouldn’t speak to any authority” in the sport.
His online rants against women have also seen him compare pundit Eni Aluko and broadcaster Lucy Ward to notorious serial killers Fred and Rose West, while claiming he would score 100 out of 100 penalties against England goalkeeper Mary Earps.
Last month he angered fans after insulting 17-year-old goalkeeper Patrick Thistle. Ava Easdon After the young man’s performance between the sticks in the Sky Sports Cup final and asked: “What’s this nonsense on the box?”
Among Barton’s most controversial comments was her claim that it was “dangerous” for women to work in men’s clubs because they “had full-blown affairs and cost people marriages.”
This is not the first time Barton has revealed trouble for his tweets, after publishing a legal letter from Aluko’s lawyers after he went on a rant about the expert.


Barton also took aim at Eni Aluko (left) and Lucy Ward (right) compared the experts to serial killers Fred and Rose West.
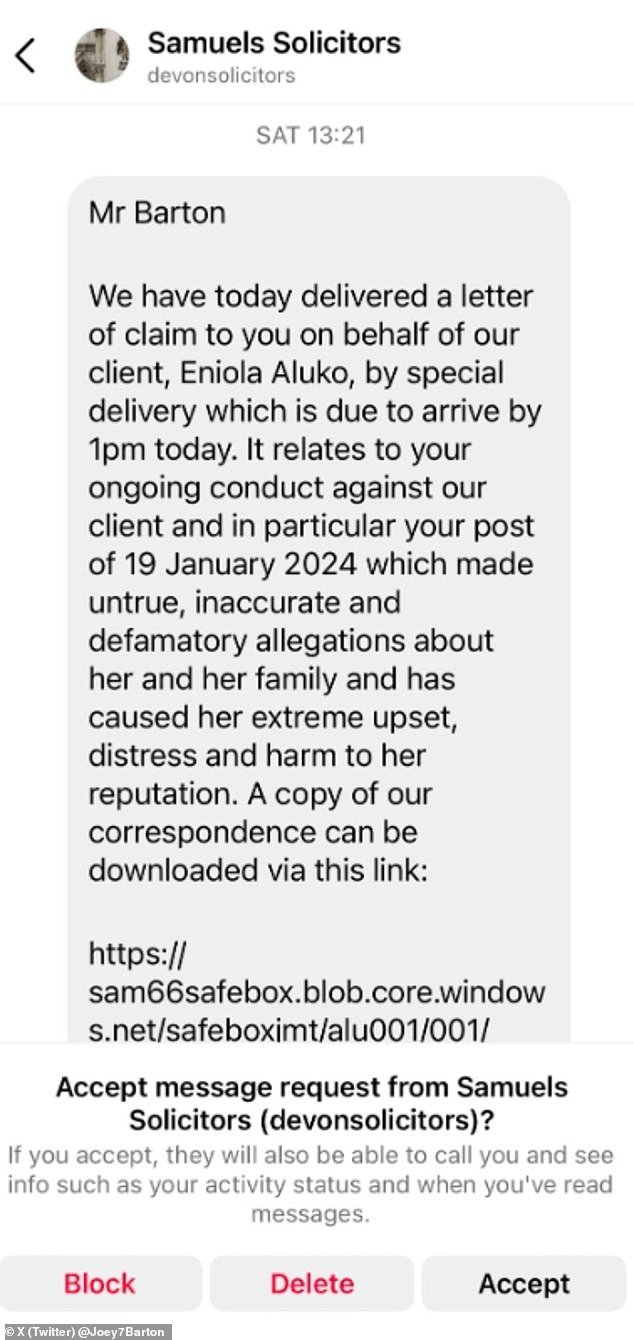
Barton took to social media to reveal messages sent by a lawyer claiming to represent Aluko.
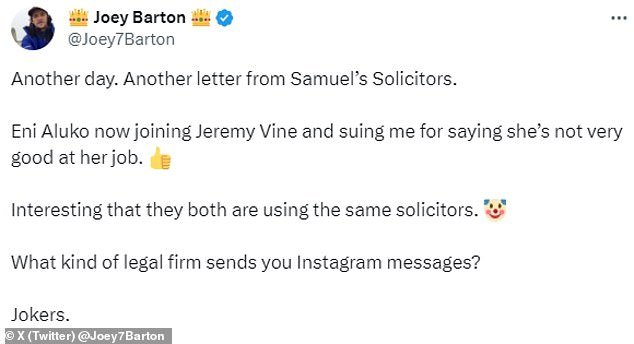
Barton wrote: ‘Another day. Another letter from Samuel’s lawyers.
‘Eni Aluko is now joining Jeremy Vine and suing me for saying she’s not very good at her job. It’s interesting that they both use the same attorneys.
What kind of law firm sends you Instagram messages? Pranksters.’
It came after Barton doubled down on comparing Aluko to Fred and Rose West by comparing her to former Soviet Union leader Joseph Stalin.
He took to
‘Had a bit of time to consider the impact of my words after @itvfootball’s big statement.
He’s clearly in the Joseph Stalin/Pol Pot category. He has murdered hundreds of thousands of football fans in recent years. ‘Meritocracy rules!’
Barton played 435 during an acrimonious career that landed him in the headlines for a series of controversial incidents.
In 2004, Barton stabbed Manchester City team member Jason Tandy in the eye with a cigarette during an alcoholic Christmas party.
Barton said his outburst was sparked after youth star Tandy provoked him, setting his shirt on fire in the run-up to the fight, leading to the football bad boy being fined six weeks’ pay and an apology. to the dejected boss Kevin. Keegan.
Four years later, Barton once again found himself in the spotlight after a training ground fight with former teammate Ousmane Dabo, in which Hardman hopeful Barton was handed a six-year suspension. matches by the FA in 2008.

