Chinese fraudsters using fake websites purporting to sell designer goods at deep discounts are believed to have made off with the credit card details and personal data of around 800,000 people in Europe and the United States, an investigation has revealed.
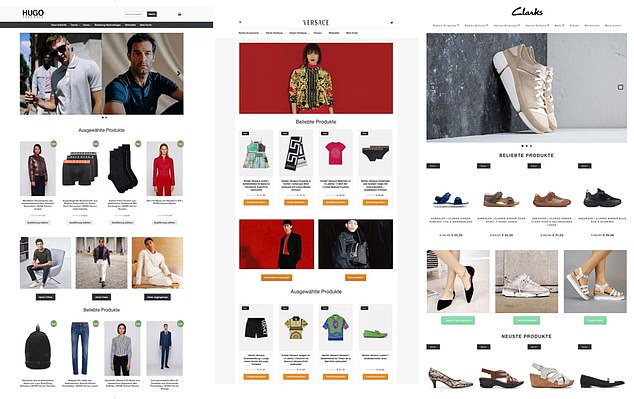
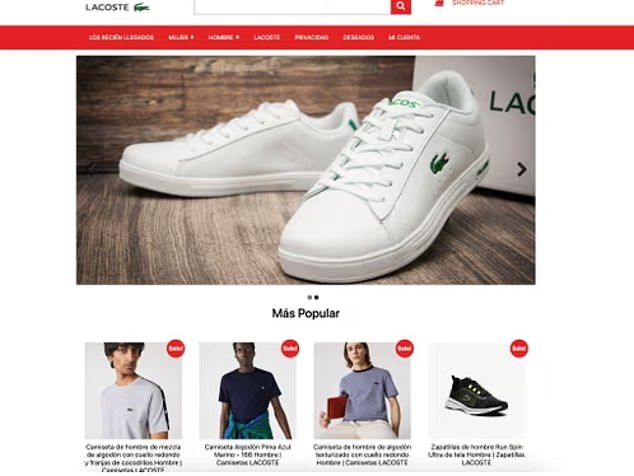
The scheme, called by a British trading standards body one of the biggest scams of its kind ever carried out, involves more than 75,000 websites bearing the logos of various high-end brands – from Nike to UNIQLO and from Paul Smith to Cartier- that claim to sell merchandise at a reduced price.
The English versions of the sites are accompanied by duplicates in several European languages, including French, German, Spanish and Italian, designed to mislead unsuspecting buyers.
And although about two-thirds of them have already been deactivated, researchers believe that more than 22,500 are still active and continue to deceive bargain-hunting online shoppers.
SR Labs, a German cybersecurity consultancy that discovered the scam, said a group of programmers appeared to have created a system to quickly generate and deploy new sites, dramatically increasing their reach.
Chinese scammers have used fake websites claiming to sell designer products at deep discounts to steal people’s data.
The Chinese group, dubbed “BogusBazaar” by SR Labs, is believed to have scammed millions of pounds, euros and dollars from its victims since launching the first sites in 2015.
Around 476,000 people are believed to have shared their debit and credit card details, including their three-digit security number.
But in many cases, scammers weren’t looking for money. Customers were often told upon payment that their bank, or the website itself, had rejected the payment request.
Although the money may have remained in their accounts, their personal details (including full name, address, credit card number and three-digit security code) were all in the hands of the scammers.
Vonny Gamot, EMEA director at online protection company McAfee, said: “Late last year, McAfee researchers saw an increase in luxury brand scams like these, including spikes of 600% over normal seasonal levels.
“Personal information is now a kind of currency because it is linked to everything from your bank accounts, investments, insurance payments and even tax returns and personal identification like driver’s licenses.”
And Jake Moore, global cybersecurity advisor at software company ESET, said The Guardian: “The big picture is that you have to assume that the Chinese government can potentially have access to the data,” he said.
Matthias Marx, a consultant at SR Labs, explained how a small team of programmers appeared to have created a system that can partially automate the generation and publishing of new versions of scam sites, helping the team scale their operation at a rapid pace.
A larger team is then hired to oversee and manage these sites in a sort of “franchise” model.
The English versions of the sites are accompanied by duplicates in several European languages, including French, German, Spanish and Italian, designed to mislead unsuspecting buyers.
He explained that a central team develops the software and supports the operation of the network, while franchisees “manage the daily operations of the fraudulent stores.”
SR Labs decided to share the results of its research with a German newspaper Timewho then worked with The Guardian and French outlet Le Monde to dig deeper.
Their research found a wide variety of brands and companies that Chinese developers used to create their scam.
Although many of the brands were high-fashion hits like Christian Dior, researchers also found sites that imitated British high street favorites like shoemaker Clarks, as well as scam pages targeting those with a penchant for the work of individual designers. .
The products they intended to sell were not limited to just fashion either.
Websites were found purporting to sell everything from children’s toys to household items and garden furniture to car parts.
The sites had no connection to the brands they claimed to sell and consumers who used them told the inquiry they never received the items they thought they had bought.
However, the sites managed to trick buyers into sharing their information.
Personal data such as that obtained during scams could be valuable to foreign intelligence agencies and for surveillance purposes.
This week it emerged that up to 272,000 UK service staff could have been affected by a data breach.
Defense Secretary Grant Shapps blamed the attack on a “malign actor” but did not confirm reports that China was behind the theft.