- Tinder says new verification options will let users know who they’re talking to
- Soon users will only be verified if they use both photo and ID verification.
Parents may have once warned against talking to strangers on the Internet.
But dating apps are now one of the most common ways for couples around the world to meet each other.
Pairing up with strangers still has its drawbacks, including the risk of being “caught.”
But help is at hand, as Tinder has launched new verification tools in the UK and US that allow users to scan their passport or driving license to confirm their identity.
“Giving users more confidence that their matches are authentic is one of the most valuable things we can do for our users,” said Rory Kozoll, senior vice president of product integrity at Tinder.
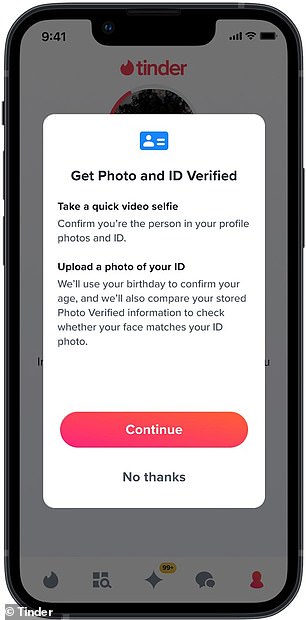
Starting this spring in the UK and Brazil and summer in the US and Mexico, users will be able to get their blue check mark by submitting a selfie video and an image of their ID.
Catfishing has been a problem for online dating for as long as the Internet has existed.
In fact, research from ExpressVPN revealed that a staggering 22 percent of Brits have been victims of catfishing in their lifetime.
Part of the reason this has become common is how easy it can be to create a fake account on many dating apps.
Without the use of identification or video verification, scammers have easily been able to take photos from social media or even Google images to create fictitious personas.
However, Tinder says its new verification system will help make dating safer for people on the app.
Expanding on the existing video verification option, users will now be invited to scan a valid driver’s license or passport.
Tinder says the new option will roll out to users in the UK and Brazil starting in the spring, while users in the US and Mexico will have access to the new option starting in the summer.
And Tinder says there’s a good incentive to go through this process.
According to its own statistics, when this feature was tested in Australia and New Zealand last year, verified accounts saw a 67 percent increase in matches.
Pamela Zaballa, chief executive of domestic and sexual violence charity NO MORE, said: “People want to feel safe and confident when connecting and communicating with their partners.”
“We applaud Tinder for offering users this additional option to help confirm that their match is the person on their profile.”

Tinder says the new measures will make the app safer and help verified users get more matches.
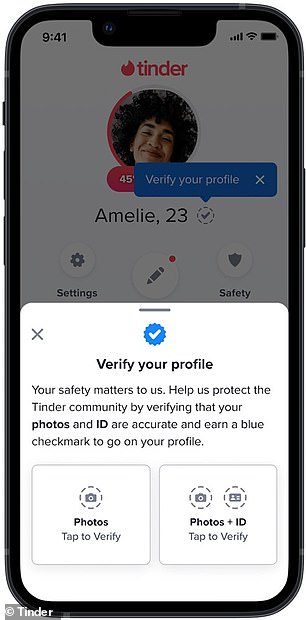
To verify your account and receive a blue check mark like on Twitter, select the “Verify your profile” option on your profile page.
You will then be asked to choose between photo or photo and ID verification.
Then, you’ll need to provide a selfie video and a photo of a government-issued ID to be verified.
This will provide confirmation of key details such as date of birth and resemblance.
Users who only use video verification will have a blue camera icon and users who only complete ID verification will receive a blue ID.
Only those users who have a photo and ID verification will receive a blue check mark next to their profile.
This update follows the highly publicized scandals of a handful of particularly prolific Tinder scammers.
In particular, so-called ‘Tinder Scammer’ Shimon Heyada Hayut scammed women out of around £7.4 million in total by posing as a multi-millionaire.
However, Tinder hopes this will make it safer for users to meet up in the real world.
Ted Bunch, development director at educational charity A Call To Men, says: “We believe identity verification is an important tool that users can adopt to help prove they are the person in their photos, as well as to provide some peace of mind when deciding to meet someone outside of the app.