Flaws in a third-party app that allows smaller airlines to upload pilots and flight crew to pre-authorized lists may have helped “fake pilots” bypass key safety checks.
The bug would have allowed malicious actors to add anyone they wanted to the known crewmember program’s database, allowing the Transportation Security Administration (TSA) to identify airline personnel who can bypass its security checkpoints.
The troubling discovery follows a TSA report indicating that 300 people have evaded airport security since March 2023 — “a higher number than we previously thought,” the agency said.
The two cybersecurity researchers, known as “bug hunters,” who found the flaw said they had privately reported the problem last April to both the Federal Aviation Administration and the U.S. Department of Homeland Security, which runs the TSA.
But only the FAA has taken appropriate action, they said, adding that “TSA’s press office issued dangerously incorrect statements about the vulnerability.”
Glitches in the third-party FlyCASS app — which allows smaller airlines to put pilots and flight crew on pre-approved TSA lists — may have helped “rogue pilots” bypass security checks, cybersecurity researchers said. Above, TSA screening in action at Denver International Airport in 2019
The couple of security researchers, Ian Carroll and Sam CurryThey said they discovered the vulnerability in the login systems of third-party website provider FlyCASS.
FlyCASS allows small airline customers to upload their crew information to both the TSA’s Known Crew Member System (KCM) and the FAA’s Cabin Access Security System (CASS).
“Anyone with basic SQL injection knowledge could log into this site and add anyone they wanted to KCM and CASS,” the duo said, “allowing them to bypass security checks and then gain access to the cockpits of commercial aircraft.”
“We realized we had discovered a very serious problem,” Carroll and Curry added.
Computer experts from the University of California at Berkeley They have described SQL injections as “one of the most common web attack mechanisms used by attackers to steal sensitive data from organizations.”
The technique exploits a common problem with the structured query language (SQL) used to host information databases on the web.
The attack allows a hacker to upload actionable SQL code into user interfaces such as contact forms on websites, or in this case, the FlyCASS web application for airlines.
Using a series of basic SQL injections, security researchers were able to gain administrative privileges for the first time in FlyCASS for the small Ohio-based cargo airline, Air Transport International.
Carroll and Curry reported that they were then able to upload a fake Air Transport International employee, named ‘Test TestOnly’ with a photo ID and were able to authorize ‘TestOnly’ for access to KCM and CASS.
TSA press secretary R. Carter Langston denied that the security investigators’ findings were as dire as the two claimed.
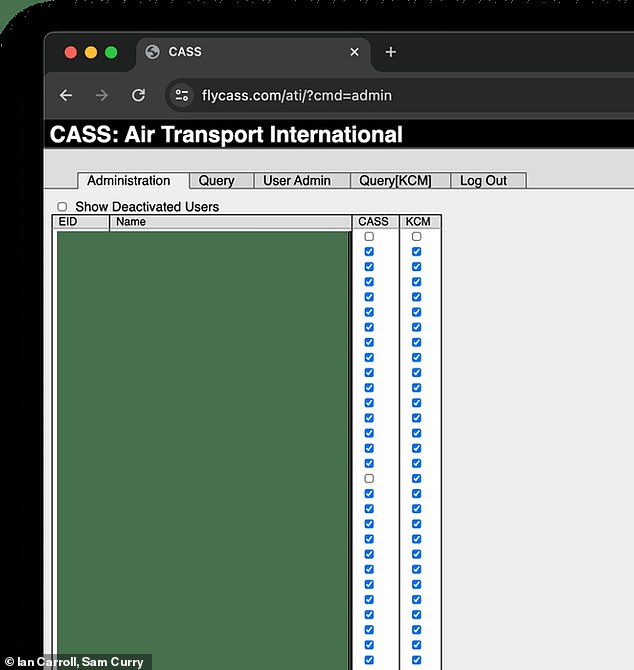
Using ‘SQL injection’ techniques, security researchers managed to gain administrative privileges on FlyCASS for the small Ohio-based cargo airline Air Transport International.
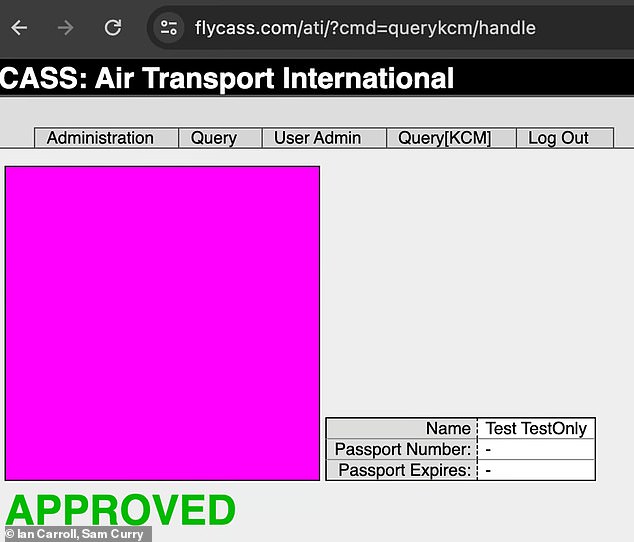
Carrol and Curry reported that they were able to upload a fake airline employee, named ‘Test TestOnly’ (above), and were able to authorize fake access to both KCM and CASS.

The two cybersecurity researchers have now also accused the TSA of issuing “dangerously incorrect statements about the vulnerability,” downplaying the risk this could pose to air traffic.
The TSA, according to Langston, “does not rely solely on this database to verify the identity of crew members.”
“TSA has procedures in place to verify the identity of crew members,” Langston said. Computer beeping‘and only verified crew members are allowed access to the secure area of airports.’
“No government data or systems were compromised and there are no impacts on transportation security related to the activities,” the agency spokesperson stressed.
In An update In their report, Carroll and Curry responded by noting that the administrator privileges they managed to obtain also allowed them to edit existing profiles in the known crewmember database, not just add new ones.
“Since our vulnerability allowed us to edit an existing KCM member,” they said, “we could have changed the photo and name of an existing registered user, which would likely bypass any vetting process that may exist for new members.”


